Tech
A third of the world’s population lacks internet connectivity − airborne communications stations could change that

Mohamed-Slim Alouini, King Abdullah University of Science and Technology and Mariette DiChristina, Boston University
About one-third of the global population, around 3 billion people, don’t have access to the internet or have poor connections because of infrastructure limitations, economic disparities and geographic isolation.
Today’s satellites and ground-based networks leave communications gaps where, because of geography, setting up traditional ground-based communications equipment would be too expensive.
High-altitude platform stations – telecommunications equipment positioned high in the air, on uncrewed balloons, airships, gliders and airplanes – could increase social and economic equality by filling internet connectivity gaps in ground and satellite coverage. This could allow more people to participate fully in the digital age.
One of us, Mohamed-Slim Alouini, is an electrical engineer who contributed to an experiment that showed it is possible to provide high data rates and ubiquitous 5G coverage from the stratosphere. The stratosphere is the second lowest layer of the atmosphere, ranging from 4 to 30 miles above the Earth. Commercial planes usually fly in the lower part of the stratosphere. The experiment measured signals between platform stations and users on the ground in three scenarios: a person staying in one place, a person driving a car and a person operating a boat.
My colleagues measured how strong the signal is in relation to interference and background noise levels. This is one of the measures of network reliability. The results showed that the platform stations can support high-data-rate applications such as streaming 4K resolution videos and can cover 15 to 20 times the area of standard terrestrial towers.
Early attempts by Facebook and Google to commercially deploy platform stations were unsuccessful. But recent investments, technological improvements and interest from traditional aviation companies and specialized aerospace startups may change the equation.
The goal is global connectivity, a cause that brought the platform stations idea recognition in the World Economic Forum’s 2024 Top 10 Emerging Technologies report. The international industry initiative HAPS Alliance, which includes academic partners, is also pushing toward that goal.
Fast, cost effective, flexible
Platform stations would be faster, more cost effective and more flexible than satellite-based systems.
Because they keep communications equipment closer to Earth than satellites, the stations could offer stronger, higher-capacity signals. This would enable real-time communications speedy enough to communicate with standard smartphones, high-resolution capabilities for imaging tasks and greater sensitivity for sensing applications. They transmit data via free-space optics, or light beams, and large-scale antenna array systems, which can send large amounts of data quickly.
Satellites can be vulnerable to eavesdropping or jamming when their orbits bring them over adversarial countries. But platform stations remain within the airspace of a single country, which reduces that risk.
High-altitude platform stations are also easier to put in place than satellites, which have high launch and maintenance costs. And the regulatory requirements and compliance procedures required to secure spots in the stratosphere are likely to be simpler than the complex international laws governing satellite orbits. Platform stations are also easier to upgrade, so improvements could be deployed more quickly.
Platform stations are also potentially less polluting than satellite mega-constellations because satellites burn up upon reentry and can release harmful metals into the atmosphere, while platform stations can be powered by clean energy sources such as solar and green hydrogen.
The key challenges to practical platform stations are increasing the amount of time they can stay aloft to months at a time, boosting green onboard power and improving reliability – especially during automated takeoff and landing through the lower turbulent layers of the atmosphere.
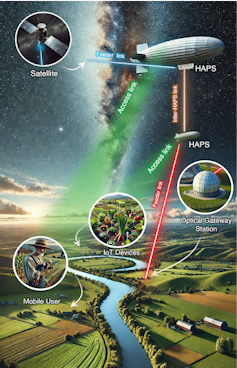
Beyond satellites
Platform stations could play a critical role in emergency and humanitarian situations by supporting relief efforts when ground-based networks are damaged or inoperative.
The stations could also connect Internet of Things (IoT) devices and sensors in remote settings to better monitor the environment and manage resources.
In agriculture, the stations could use imaging and sensing technologies to help farmers monitor crop health, soil conditions and water resources.
Their capability for high-resolution imaging could also support navigation and mapping activities crucial for cartography, urban planning and disaster response.
The stations could also do double duty by carrying instruments for atmospheric monitoring, climate studies and remote sensing of Earth’s surface features, vegetation and oceans.
From balloons to airplanes
Platform stations could be based on different types of aircraft.
Balloons offer stable, long-duration operation at high altitudes and can be tethered or free-floating. Airships, also known as dirigibles or blimps, use lighter-than-air gases and are larger and more maneuverable than balloons. They’re especially well suited for surveillance, communications and research.
Gliders and powered aircraft can be controlled more precisely than balloons, which are sensitive to variations in wind speed. In addition, powered aircraft, which include drones and fixed-wing airplanes, can provide electricity to communication equipment, sensors and cameras.
Next-generation power
Platform stations could make use of diverse power sources, including increasingly lightweight and efficient solar cells, high-energy-density batteries, green hydrogen internal combustion engines, green hydrogen fuel cells, which are now at the testing stage, and eventually, laser beam powering from ground- or space-based solar stations.
The evolution of lightweight aircraft designs coupled with advancements in high-efficiency motors and propellers enable planes to fly longer and carry heavier payloads. These cutting-edge lightweight planes could lead to platform stations capable of maneuvering in the stratosphere for extended periods.
Meanwhile, improvements in stratospheric weather models and atmospheric models make it easier to predict and simulate the conditions under which the platform stations would operate.
Bridging the global digital divide
Commerical deployment of platform stations, at least for post-disaster or emergency situations, could be in place by the end of the decade. For instance, a consortium in Japan, a country with remote mountainous and island communities, has earmarked US$100 million for solar-powered, high-altitude platform stations.
Platform stations could bridge the digital divide by increasing access to critical services such as education and health care, providing new economic opportunities and improving emergency response and environmental monitoring. As advances in technology continue to drive their evolution, platform stations are set to play a crucial role in a more inclusive and resilient digital future.
Mohamed-Slim Alouini, Distinguished Professor of Electrical and Computer Engineering, King Abdullah University of Science and Technology and Mariette DiChristina, Dean and Professor of the Practice in Journalism, College of Communication, Boston University
This article is republished from The Conversation under a Creative Commons license. Read the original article.
STM Daily News is a vibrant news blog dedicated to sharing the brighter side of human experiences. Emphasizing positive, uplifting stories, the site focuses on delivering inspiring, informative, and well-researched content. With a commitment to accurate, fair, and responsible journalism, STM Daily News aims to foster a community of readers passionate about positive change and engaged in meaningful conversations. Join the movement and explore stories that celebrate the positive impacts shaping our world.
Discover more from Daily News
Subscribe to get the latest posts sent to your email.
Tech
When ‘Head in the Clouds’ Means Staying Ahead
Head in the Clouds: Cloud is no longer just storage—it’s the intelligent core of modern business. Explore how “cognitive cloud” blends AI and cloud infrastructure to enable real-time, self-optimizing operations, improve customer experiences, and accelerate enterprise modernization.
Last Updated on February 7, 2026 by Daily News Staff

When ‘Head in the Clouds’ Means Staying Ahead
(Family Features) You approve a mortgage in minutes, your medical claim is processed without a phone call and an order that left the warehouse this morning lands at your door by dinner. These moments define the rhythm of an economy powered by intelligent cloud infrastructure. Once seen as remote storage, the cloud has become the operational core where data, AI models and autonomous systems converge to make business faster, safer and more human. In this new reality, the smartest companies aren’t looking up to the cloud; they’re operating within it. Public cloud spending is projected to reach $723 billion in 2025, according to Gartner research, reflecting a 21% increase year over year. At the same time, 90% of organizations are expected to adopt hybrid cloud by 2027. As cloud becomes the universal infrastructure for enterprise operations, the systems being built today aren’t just hosted in the cloud, they’re learning from it and adapting to it. Any cloud strategy that doesn’t account for AI workloads as native risks falling behind, holding the business back from delivering the experiences consumers rely on every day. After more than a decade of experimentation, most enterprises are still only partway up the curve. Based on Cognizant’s experience, roughly 1 in 5 enterprise workloads has moved to the cloud, while many of the most critical, including core banking, health care claims and enterprise resource planning, remain tied to legacy systems. These older environments were never designed for the scale or intelligence the modern economy demands. The next wave of progress – AI-driven products, predictive operations and autonomous decision-making – depends on cloud architectures designed to support intelligence natively. This means cloud and AI will advance together or not at all.The Cognitive Cloud: Cloud and AI as One System
For years, many organizations treated migration as a finish line. Applications were lifted and shifted into the cloud with little redesign, trading one set of constraints for another. The result, in many cases, has been higher costs, fragmented data and limited room for innovation. “Cognitive cloud” represents a new phase of evolution. Imagine every process, from customer service to supply-chain management, powered by AI models that learn, reason and act within secure cloud environments. These systems store and interpret data, detect patterns, anticipate demand and automate decisions at a scale humans simply cannot match. In this architecture, AI and cloud operate in concert. The cloud provides computing power, scale and governance while AI adds autonomy, context and insight. Together, they form an integrated platform where cloud foundations and AI intelligence combine to enable collaboration between people and systems. This marks the rise of the responsive enterprise; one that senses change, adjusts instantly and builds trust through reliability. Cognitive cloud platforms combine data fabric, observability, FinOps and SecOps into an intelligent core that regulates itself in real time. The result is invisible to consumers but felt in every interaction: fewer errors, faster responses and consistent experiences.Consumer Impact is Growing
The impact of cognitive cloud is already visible. In health care, 65% of U.S. insurance claims run through modernized, cloud-enabled platforms designed to reduce errors and speed up reimbursement. In the life sciences industry, a pharmaceuticals and diagnostics firm used cloud-native automation to increase clinical trial investigations by 20%, helping get treatments to patients sooner. In food service, intelligent cloud systems have reduced peak staffing needs by 35%, in part through real-time demand forecasting and automated kitchen operation. In insurance, modernization has produced multi-million-dollar savings and faster policy issuance, improving both customer experience and financial performance. Beneath these outcomes is the same principle: architecture that learns and responds in real time. AI-driven cloud systems process vast volumes of data, identify patterns as they emerge and automate routines so people can focus on innovation, care and service. For businesses, this means fewer bottlenecks and more predictive operations. For consumers, it means smarter, faster, more reliable services, quietly shaping everyday life. While cloud engineering and AI disciplines remain distinct, their outcomes are increasingly intertwined. The most advanced architectures now treat intelligence and infrastructure as complementary forces, each amplifying the other.Looking Ahead
This transformation is already underway. Self-correcting systems predict disruptions before they happen, AI models adapt to market shifts in real time and operations learn from every transaction. The organizations mastering this convergence are quietly redefining themselves and the competitive landscape. Cloud and AI have become interdependent priorities within a shared ecosystem that moves data, decisions and experiences at the speed customers expect. Companies that modernize around this reality and treat intelligence as infrastructure will likely be empowered to reinvent continuously. Those that don’t may spend more time maintaining the systems of yesterday than building the businesses of tomorrow. Learn more at cognizant.com. Photo courtesy of ShutterstockCulver’s Thank You Farmers® Project Hits $8 Million Donation MilestoneLink: https://stmdailynews.com/culvers-thank-you-farmers-project-hits-8-million-donation-milestone/
Discover more from Daily News
Subscribe to get the latest posts sent to your email.
The Knowledge
Beneath the Waves: The Global Push to Build Undersea Railways
Undersea railways are transforming transportation, turning oceans from barriers into gateways. Proven by tunnels like the Channel and Seikan, these innovations offer cleaner, reliable connections for passengers and freight. Ongoing projects in China and Europe, alongside future proposals, signal a new era of global mobility beneath the waves.

For most of modern history, oceans have acted as natural barriers—dividing nations, slowing trade, and shaping how cities grow. But beneath the waves, a quiet transportation revolution is underway. Infrastructure once limited by geography is now being reimagined through undersea railways.
Undersea rail tunnels—like the Channel Tunnel and Japan’s Seikan Tunnel—proved decades ago that trains could reliably travel beneath the ocean floor. Today, new projects are expanding that vision even further.
Around the world, engineers and governments are investing in undersea railways—tunnels that allow high-speed trains to travel beneath oceans and seas. Once considered science fiction, these projects are now operational, under construction, or actively being planned.

Undersea Rail Is Already a Reality
Japan’s Seikan Tunnel and the Channel Tunnel between the United Kingdom and France proved decades ago that undersea railways are not only possible, but reliable. These tunnels carry passengers and freight beneath the sea every day, reshaping regional connectivity.
Undersea railways are cleaner than short-haul flights, more resilient than bridges, and capable of lasting more than a century. As climate pressures and congestion increase, rail beneath the sea is emerging as a practical solution for future mobility.
What’s Being Built Right Now
China is currently constructing the Jintang Undersea Railway Tunnel as part of the Ningbo–Zhoushan high-speed rail line, while Europe’s Fehmarnbelt Fixed Link will soon connect Denmark and Germany beneath the Baltic Sea. These projects highlight how transportation and technology are converging to solve modern mobility challenges.
The Mega-Projects Still on the Drawing Board
Looking ahead, proposals such as the Helsinki–Tallinn Tunnel and the long-studied Strait of Gibraltar rail tunnel could reshape global affairs by linking regions—and even continents—once separated by water.
Why Undersea Rail Matters
The future of transportation may not rise above the ocean—but run quietly beneath it.
Discover more from Daily News
Subscribe to get the latest posts sent to your email.
CES 2026
Inside the Computing Power Behind Spatial Filmmaking: Hugh Hou Goes Hands-On at GIGABYTE Suite During CES 2026
Inside the Computing Power Behind Spatial Filmmaking: Hugh Hou Goes Hands-On at GIGABYTE Suite During CES 2026
Spatial filmmaking is having a moment—but at CES 2026, the more interesting story wasn’t a glossy trailer or a perfectly controlled demo. It was the workflow.
According to a recent GIGABYTE press release, VR filmmaker and educator Hugh Hou ran a live spatial computing demonstration inside the GIGABYTE suite, walking attendees through how immersive video is actually produced in real-world conditions—capture to post to playback—without leaning on pre-rendered “best case scenario” content. In other words: not theory, not a lab. A production pipeline, running live, on a show floor.

A full spatial pipeline—executed live
The demo gave attendees a front-row view of a complete spatial filmmaking pipeline:
- Capture
- Post-production
- Final playback across multiple devices
And the key detail here is that the workflow was executed live at CES—mirroring the same processes used in commercial XR projects. That matters because spatial video isn’t forgiving. Once you’re working in 360-degree environments (and pushing into 8K), you’re no longer just chasing “fast.” You’re chasing:
- System stability
- Performance consistency
- Thermal reliability
Those are the unsexy requirements that make or break actual production days.
Playback across Meta Quest, Apple Vision Pro, and Galaxy XR
The session culminated with attendees watching a two-minute spatial film trailer across:
- Meta Quest
- Apple Vision Pro
- Newly launched Galaxy XR headsets
- Plus a 3D tablet display offering an additional 180-degree viewing option
That multi-device playback is a quiet flex. Spatial content doesn’t live in one ecosystem anymore—creators are being pulled toward cross-platform deliverables, which adds even more pressure on the pipeline to stay clean and consistent.
Where AI fits (when it’s not the headline)
One of the better notes in the release: AI wasn’t positioned as a shiny feature. It was framed as what it’s becoming for a lot of editors—an embedded toolset that speeds up the grind without hijacking the creative process.
In the demo, AI-assisted processes supported tasks like:
- Enhancement
- Tracking
- Preview workflows
The footage moved through industry-standard software—Adobe Premiere Pro and DaVinci Resolve—with AI-based:
- Upscaling
- Noise reduction
- Detail refinement
And in immersive VR, those steps aren’t optional polish. Any artifact, softness, or weird noise pattern becomes painfully obvious when the viewer can look anywhere.
Why the hardware platform matters for spatial workloads
Underneath the demo was a custom-built GIGABYTE AI PC designed for sustained spatial video workloads. Per the release, the system included:
- AMD Ryzen 7 9800X3D processor
- Radeon AI PRO R9700 AI TOP GPU
- X870E AORUS MASTER X3D ICE motherboard
The point GIGABYTE is making is less “look at these parts” and more: spatial computing workloads demand a platform that can run hard continuously—real-time 8K playback and rendering—without throttling, crashing, or drifting into inconsistent performance.
That’s the difference between “cool demo” and “reliable production machine.”
The bigger takeaway: spatial filmmaking is moving from experiment to repeatable process
By running a demanding spatial filmmaking workflow live—and repeatedly—at CES 2026, GIGABYTE is positioning spatial production as something creators can depend on, not just test-drive.
And that’s the shift worth watching in 2026: spatial filmmaking isn’t just about headsets getting better. It’s about the behind-the-scenes pipeline becoming stable enough that creators can treat immersive production like a real, repeatable craft—because the tools finally hold up under pressure.
Source:PRNewswire – GIGABYTE press release
Welcome to the Consumer Corner section of STM Daily News, your ultimate destination for savvy shopping and informed decision-making! Dive into a treasure trove of insights and reviews covering everything from the hottest toys that spark joy in your little ones to the latest electronic gadgets that simplify your life. Explore our comprehensive guides on stylish home furnishings, discover smart tips for buying a home or enhancing your living space with creative improvement ideas, and get the lowdown on the best cars through our detailed auto reviews. Whether you’re making a major purchase or simply seeking inspiration, the Consumer Corner is here to empower you every step of the way—unlock the keys to becoming a smarter consumer today!
https://stmdailynews.com/category/consumer-corner
Discover more from Daily News
Subscribe to get the latest posts sent to your email.
